Overview:
Today’s borderless networks are redefining endpoint protection. With a variety of endpoints freely accessing networks, they’re storing sensitive corporate data. Because 70 percent of successful data breaches start on endpoints, a preventative approach to endpoint security can help stop cyber attacks. SandBlast Agent is the advanced endpoint protection and threat prevention solution to protect your organization.

Innovative Threat Prevention Technologies
Uses static, dynamic, and behavioral detection and prevention technologies with advanced artificial intelligence to provide high catch rates and low false positives
Insightful Detection and Response
Assures continuous collection of comprehensive and complete raw forensics data, employing full attack remediation capabilities

Complete Endpoint Security Solution
Integrates into Check Point Infinity to get maximum prevention across all attack surfaces, shared intelligence, and a single point of management (cloud service or on premise)
Benefits:
Unified endpoint security management reduces security gaps
- Unify all endpoint security protection in a single management console
- Straightforward policy language focused on business processes
- Comprehensive, immediate security with preconfigured, customizable policies
- Integrated into Check Point Software Blade Architecture for on-demand security
Maximum visibility and control of security and at-a-glance dashboard
- Manage security for entire organizations, groups, users and their devices
- Enforce and remediate endpoint compliance before accessing network
- Search for security events across network and endpoints
- Manage endpoint and network security from one management appliance
Policy management and security for users, not just machines
- Drill-down on users and all their associated machines to investigate status
- Apply security policy to users, no matter what machine they log into
- Modify, track and report policy changes at all levels of the organization
- Use AD or customize your own organizational structure for policy enforcement
Features:
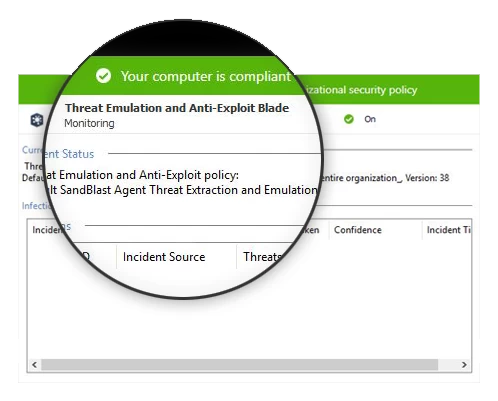
Threat Emulation
Evasion-resistant sandbox technology detects malicious behavior and prevents potential attacks
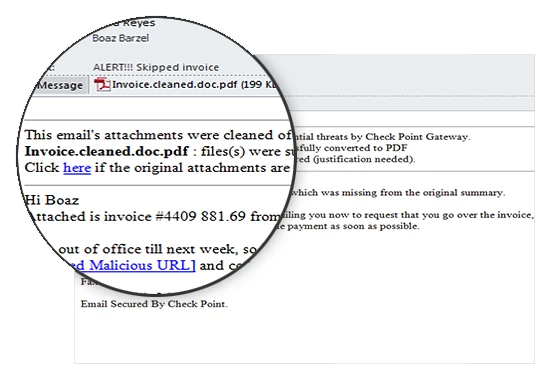
Threat Extraction
Reconstructs downloaded files, delivering clean, risk-free files to users in real time
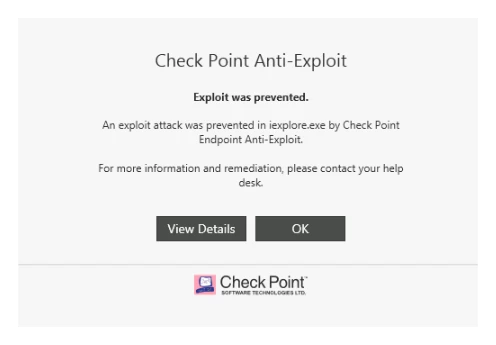
Anti-Exploit
Protects and prevents vulnerable applications and systems from exploit attacks
Anti-Bot
Detects, contains, and remediates infected hosts
Zero-Phishing
Blocks deceptive phishing sites and alerts on password reuse in real time
Behavioral Guard
Prevents, delects, and remediates even the most evasive attacks
Anti-Ransomware
Detects and quarantines the most evasive ransomware variants
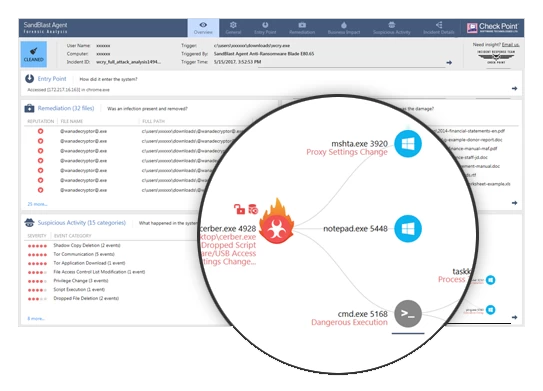
Forensics
Records and analyzes all endpoint events to provide actionable attack forensic report
Anti-Malware
Protects endpoints from known viruses, worms, and Trojan horse malware and it serves as the baseline endpoint threat prevention engine against known attacks using signature and heuristics.
Full Disk Encryption
Provides maximum data protection by automatically encrypting all information on the hard drive, including user data, operating system files, and temporary and erased files. Combines pre-boot protection, boot authentication, and strong encryption to make sure that only authorised users are given access to information stored on desktops and laptops. Blocks unauthorised attempts to copy individual files or introduce rogue programs.
Media Encryption and Port Protection
Protects data stored on the computers by encrypting removable media devices and allowing tight control over computers’ ports (USB, Bluetooth, and so on).
Remote Access VPN
Provides secure, seamless, and remote access to corporate networks.
Firewall and Compliance Check
Stops unwanted traffic, prevents malware, and blocks targeted attacks, ensuring protected computers comply with security requirements; assigns different security levels according to the compliance state of the endpoint computer.
Cloud Management or On-premise
SandBlast Agent offers unified, scalable, and granular management available as a cloud service or installed on your premise.
- Unified - Manage all your endpoint security needs from a single console
- Scalable - Use one management infrastructure to manage your endpoints, from a few to hundreds of thousand devices
- Granular - Choose the management granularity that fits your needs. Relay product best practices based on defaults; go deeper by configuring everything on your system, or anywhere in between
SandBlast Agent cloud management service is fully deployed,maintained, and optimized by Check Point enabling rapid deployment, elastic growth, continuous updates and location independent.


![]()
![]()
![]()









